
Hackers Vs Hackers - Equation Group's Cyber Weapons Leaked
One week ago in Pastebin website, a new paste titled:"Equation Group - Cyber Weapons Auction", has been posted.
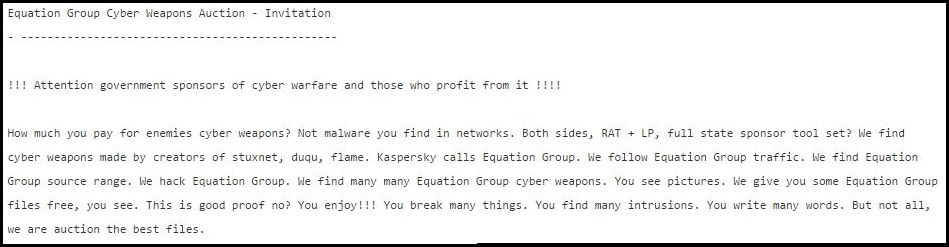
This paste seems to be published by a group of hackers called Shadow Brokers.
The group claimed to have attack tools and exploits which is probably attributable to hacker group known like "Equation Group", likely linked NSA.
Data, including exploits and hacking tools, were published on their Github and Tumblr, but the accounts were promptly suspended. These links to two distinct PGP-encrypted archives.
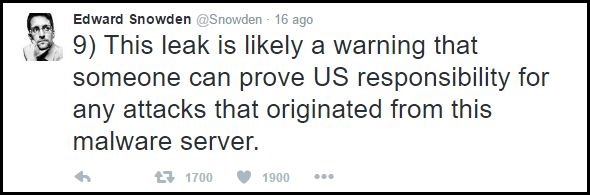
According to the information published by Edward Snowden, USA have the responsibility for these attacks.
In the leak, we found some link with some of the hacking tools names used in the documents leaked by Edward Snowden, like "BANANAGLEE" and "EPICBANANA".
The Intercept, on last Friday, published a new set of documents from the Edward Snowden archive. These documents confirms that the files leaked by the Shadow Brokers contain authentic NSA software and hacking tools used to secretly infect computers worldwide.
Archive Analysis
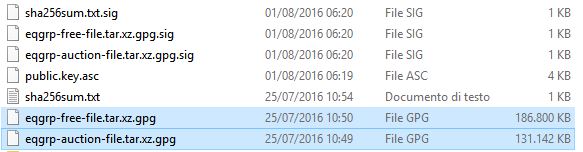
The archive has two files:
- eqgrp-free-file.xz.gpg, Shadow Brokers group released the password for free to give evidence about the leak.
- eqgrp-auction-file.xz.gpg, Shadow Brokers group auction off the password for this archive (they are asking for 1 Million Bitcoins in an auction to release the cyber weapons and more files belonging to the arsenal of the Equation Group).
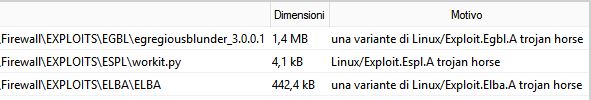
Extracting free archive in my windows lab, immediately my AV triggered three warnings about three trojan horse:
- egregiousblunder_3.0.0.1
- workit.py
- ELBA (it is a compiled version of ELBA.sh)
To avoid to have my lab compromised, I decided to switch to my linux lab and extract the archive there.
Freely distributed archive contains a small amount of information that does not directly indicate the data belonging to the Equation Group.
The exploits appear to be targeting firewalls, particularly Cisco PIX/ASA, Juniper Netscreen, Fortigate, and more.
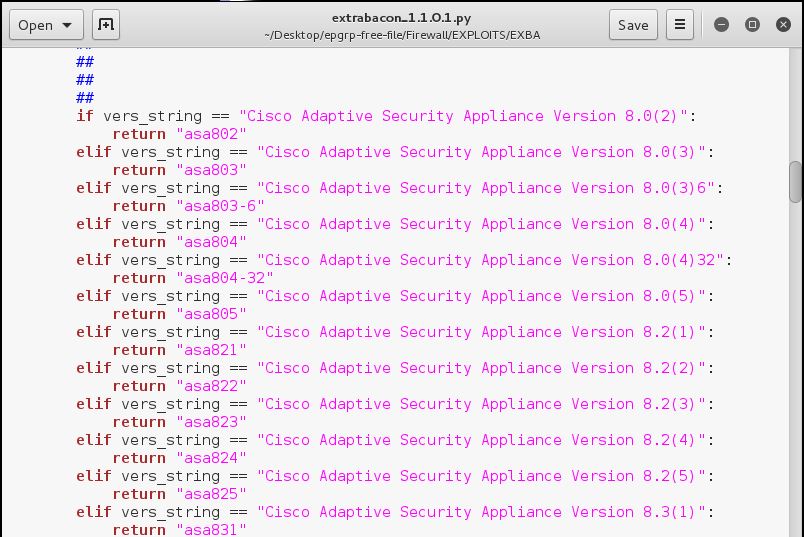
Checking the files, is possible to identify a "extrabacon_1.1.0.1", python file, where is present a piece of code that contains if-else cascading to check Cisco appliance version.
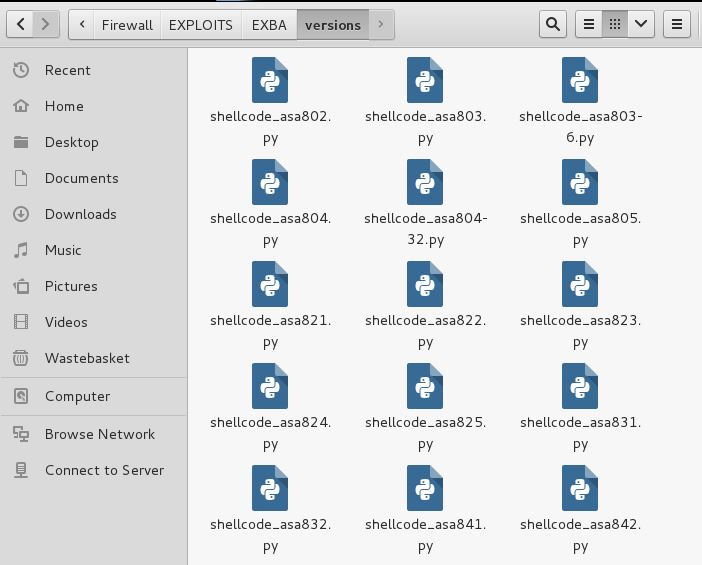
The image below report the shellcode files for each Cisco ASA version.
ExtraBacon Exploit contains a zero-day vulnerability (CVE-2016-6366) that affect the source code of Cisco ASA software that manage Simple Network Management Protocol (SNMP). This vulnerabilty could allow an unauthenticated remote attacker to cause a reboot the of the system (Quote:. Cisco advisory).
American Security Firm, like Cisco, Fortinet, Juniper and also an Cina Firm, like TopSec, have released patchs to fix these vulnerability.
Finally, this report evidences how third part market that give you the opportunity to download APK for free, could spread malicious App. To protect yourself from possible infections, download apps from official app store and not from third-party site.
If everything is true, we are officially in a cyber warfare!!
